If you have a Virginia Tech AWS account, you’ll realize there isn’t much pre-configured on the account (we’re working to change that though). To ensure proper security of the account, you should leverage the VT Login system! Why?
- No local accounts means no credentials to be compromised
- Easier on-boarding! Simply add new people to the appropriate ED groups and they have access to the cloud accounts
- Accounts are tied to the VT account lifecycle. If someone leaves your team, you know their access to the cloud accounts has also been revoked
Some Prerequisites
The only requirement is to create ED groups for the various accounts/roles you want. A couple of things to keep in mind regarding your groups:
- The ED group and AWS role will exactly match. If you have a group named
devcom.aws.adminthat you want to use, your AWS role will use the same name. - The same ED group can be used for multiple accounts. But, you can’t use the same ED group for multiple roles in the same account.
- It might be wise to include a reference to the account name in the group, letting you create roles per account. For example,
devcom.aws.123456789012.adminmight indicate admins of the123456789012account. Since the numbers are often hard to remember, you can also use an account alias (such asdevcom.aws.demo-acct.admin) - Nested groups are not currently flattened through the SAML process. While the ED allows groups to be members of other groups, members of the children groups are not exposed as members of the parent group in the SAML flow. You will need to explicitly add children group members to the parent group (or use the Terraform provider which we’ll write about soon)
Defining the SAML Provider and Roles
To make things easier, we have create a AWS VT Auth Integration Terraform module that will create the provider and the appropriate roles in your account. To use it, simply add the module to your Terraform code.
module "vt_auth" {
source = "git@code.vt.edu:devcom/terraform-modules/aws-vt-auth-integration.git"
roles = {
admin = "devcom.aws.123456789012.admin"
}
}
This will create the following:
- The SAML Identify Provider with all of the necessary metadata for VT Login
- An IAM role named
devcom.aws.123456789012.admin
The Terraform module provides all of the roles as module outputs, letting you easily attach policies on what that role can do. The roles are referenced using the keys listed in the roles map. As an example, we are going to give the admin role listed above the AWS-managed AdministratorAccess policy. You are welcome to create your own policies and attach them as you see fit.
resource "aws_iam_role_policy_attachment" "sample_attachment" {
role = module.vt_auth.roles["admin"].name
policy_arn = "arn:aws:iam::aws:policy/AdministratorAccess"
}
Final Configuration and Access
Once the roles are defined, you need to notify Middleware of the account/roles being used. They will then perform the necessary configuration to ensure you can use the ED groups. Instructions to notify Middleware can be found here.
Afterwards, you can login using the following link. You’ll be presented with a page letting you choose the role you wish to assume: https://login.vt.edu/profile/SAML2/Unsolicited/SSO?providerId=urn:amazon:webservices
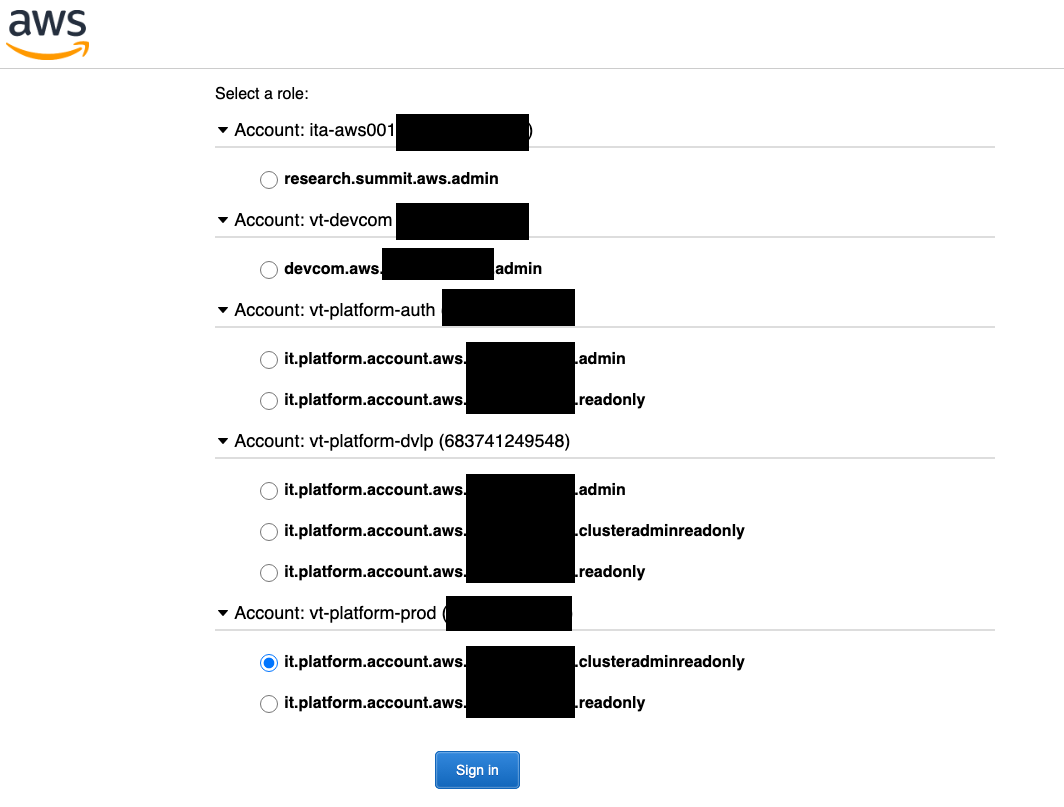
AWS SAML Login page showing several roles the user can assume across various accounts
Next Steps
Now that you have SAML-based auth on your AWS account, how do you configure your local AWS client? Hold tight, as another blog post is coming about that!